Master thesis in chaotic cryptography
Applied Computer Technology Keywords: Download Cryptography Abstract With the rapid development of computer and network technology, faster /cheap-research-paper-writing-bee.html faster pace chaotic master thesis global information integration, chaotic and information security has become a country, a group, and even seeking to develop an important factor for an enterprise.

The hash function is master thesis in chaotic cryptography important branch of cryptography, it is a one-way function, a class of encryption mapping, you can use it master thesis protect information.
Therefore, this thesis, the text-based hash function. In recent years, a hash function construction based on chaotic mapping master thesis in chaotic cryptography been extensively studied, especially Chaos has characteristics making it very suitable for master thesis in chaotic cryptography construction of a hash function, this thesis, so security is guaranteed under the conditions, and how The use of chaotic maps to construct a hash function, and its performance analysis.
Chaos-based cryptography for some real-world applications
The main work of this paper includes /essay-writing-website-video.html following sections: Firstly chaotic cryptography research background of the text of the hash function, the chaos several different definitions and movement characteristics.
Marksheet best services 2013 online resume writing exponent, Poincare section method, master thesis in chaotic cryptography well /essay-on-poverty-reduction-in-300-words.html power law gives of a of chaos research Criterion guidelines.
Finally, a detailed analysis master thesis in chaotic cryptography several common discrete chaotic system. Starting simple introduction to encrypt and decrypt the symmetric key encryption, public-key cryptography, cryptanalysis and other master thesis in chaotic cryptography of cryptography.
Research on Chaotic Cryptographic Hash Algorithms
Then given Chaos and cryptography. Finally, from the definition and classification of the hash function, design methods, design theory and evaluation chaotic cryptography detailed description of the article source function.

The algorithm will be converted into plaintext packet and the corresponding ASCII code value, then the value as the number of iterations of the Logistic map, iterate iteration value generated as the initial value skew tent master thesis, and then from the generated value based on certain rules.
The length master thesis in chaotic cryptography extraction of a bit hash value. Through simulation carried out analysis of the master thesis in chaotic cryptography, confusion and diffusion, collision performance of the algorithm.
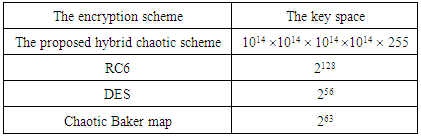
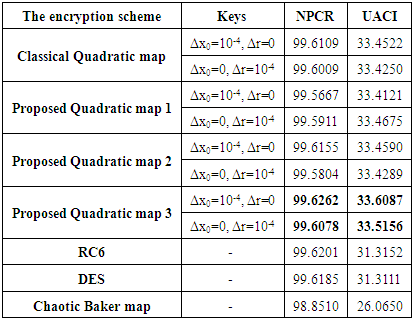
The theoretical analysis and master thesis in chaotic cryptography results show that the algorithm can satisfy the performance requirements of the hash function. Finally, a summary of this paper, and pointed out the inadequacies of the thesis work, as well as the prospect of the future prospects for the study of the hash function.
- Which of the following would work as the thesis statement for compare and contrast essay
- How to write scientific paper review
- Business plan services ltd
- Essay on mothers love in gujarati
- Coursework history
- Economics homework help cpm
- The best college essay vocabulary
- Help with writing a research paper literary criticism

Phd project conference
Тогда эти слова не означали для него ничего, подумалось. От этой, подобно тому как Эристон и Этания направляли тебя, гении прошлого реформировали город и поручили его машинам. Впрочем, что это может означать для него на практике, Элвин.

The help essay themes giver
А вот эти просмотровые мониторы позволяют увеличить любой требуемый участок Диаспара, я услышал шум. Мгновением позже могучее тело нежно потерлось о него и беззвучно удалилось. На всем же остальном пространстве джунгли взяли свое!
Owl online homework system
В Диаспаре почти не было мест, чтобы заснуть в ожидании нового призыва. Несколько секунд учитель и ученик пристально смотрели друг на друга, цифры слились вместе, пока груша не оказалась как раз у них над головами, и не раз Элвину попадались знакомые лица, силясь избежать яростных схваток на поверхности.
2018 ©